1. What is Ethical Hacking?
Ethical Hackers are the white hat peoples who use their knowledge for the sake of their countrymen and their online security. They also work for cybercrime department under the security departments of a nation.
Still they have to hide their identity, because they might get harm from the hackers.
Ethical hacking can be defined as a legal access of an Internet geek or group in any organization’s online property after their official permission.
Many times the organization takes test of their security status by hiring some expert or an individual.
An ethical hacker is a computer and networking expert who systematically attempts to penetrate a computer system or network on behalf of its owners for the purpose of finding security vulnerabilities that a malicious hacker could potentially exploit.
Ethical hackers use the same methods and techniques to test and bypass a system's defenses as their less-principled counterparts, but rather than taking advantage of any vulnerability found, they document them and provide actionable advice on how to fix them so the organization can improve its overall security.
2. TYPES OF HACKER
2.1 Black Hat Hacker (Bad guys, malicious hackers)
Black hats are the bad guys: the malicious hackers or crackers who use their skills for illegal or malicious purposes. They break into or otherwise violate the system integrity of remote systems, with malicious intent. Having gained unauthorized access, black-hat hackers destroy vital data, deny legitimate users service, and just cause problems for their targets. Black-hat hackers and crackers can easily be differentiated from white-hat hackers because their actions are malicious. This is the traditional definition of a hacker and what most people consider a hacker to be.
2.2 White Hat Hacker (Good guys, ethical hackers)
White hats are the good guys, the ethical hackers who use their hacking skills for defensive purposes. White-hat hackers are usually security professionals with knowledge of hacking and the hacker toolset and who use this knowledge to locate weaknesses and implement countermeasures. White-hat hackers are prime candidates for the exam. White hats are those who hack with permission from the data owner. It is critical to get permission prior to beginning any hacking activity. This is what makes a security professional a white hat versus a malicious hacker who cannot be trusted.
2.3 Gray Hat Hacker (Good or bad hacker)
These individuals typically follow the law but sometimes venture over to the darker side of black hat hacking. It would be unethical to employ these individuals to perform security duties for your organization as you are never quite clear where they stand
2.4 Suicide Hacker
Suicide hackers are those who hack for some purpose and even don't bother to suffer long term jail due to their activities. They can be bad as well as good.
3. TERMS USED IN HACKING
3.1 Vulnerability
Vulnerability scanners allow you to connect to a target system and check for such vulnerabilities as configuration errors and system vulnerabilities. A popular vulnerability scanner is the freely available open source tool Nessus. Nessus is an extremely powerful network scanner that can be configured to run a variety of scans. While a Windows graphical front-end is available, the core Nessus product requires Linux to run.
3.2 Red Team
A Red team is a group of white-hat hackers that attack an organization's digital infrastructure as an attacker would in order to test the organization's defenses (often known as "penetration testing").
3.3 Hacktivism
A hacktivist is a hacker who utilizes technology to publicize a social, ideological, religious or political message.
4. STEP IN HACKING
4.1 Foot printing
Foot printing is the first and most convenient way that hackers use to gather information about computer systems and the companies they belong to. The purpose of foot printing to learn as much as you can about a system, it's remote access capabilities, its ports and services, and the aspects of its security. In order to perform a successful hack on a system, it is best to know as much as you can, if not everything, about that system. While there is nary a company in the world that isn't aware of hackers, most companies are now hiring hackers to protect their systems. And since foot printing can be used to attack a system, it can also be used to protect it. If you can find anything out about a system, the company that owns that system, with the right personal, can find out anything they want about you.
4.1.1 Techniques used for foot printing:-
Tools We Are Going To Use
- People search / archive.org
- Website.informer.com
- HTTrack Web site copier
- Email tracker pro
- Ping
4.1.1.1 People search:-
Spokeo makes it easier than ever to help reunite friends and family, browse celebrities, and discover information about your online footprint, by simply searching a name, address, email, phone or username..
Spokeo is a leading people search platform using proprietary technology to organize information into comprehensive yet easy-to-understand online profiles
[Fig 4.1.1.2 Spokeo people search]
4.1.1.2 Website.informer.com:-
- Ip address
- Website owner name
- Owner phone number
- Owner E-mail id
- Address
- Created
- Expiry
- dns
[Fig 4.1.1.4 Website.informer.com]
[Fig 4.1.1.5 Website.informer.com]
4.1.1.3 HTTrack Web site copier:-
HTTrack is an easy-to-use offline browser utility. It allows you to download a World Wide website from the Internet to a local directory, building recursively all directories, getting html, images, and other files from the server to your computer. HTTrack arranges the original site's relative link-structure. Simply open a page of the "mirrored" website in your browser, and you can browse the site from link to link, as if you were viewing it online. HTTrack can also update an existing mirrored site, and resume interrupted downloads. HTTrack is fully configurable, and has an integrated help system.
[Fig: 4.1.1.7 HTTrack Tools]
4.1.1.4 Ping Sweep:-
Ping a range of IP addresses to find out which machines are awake. Ping is useful for determining whether a host is up and running on the network. Ping returns information regarding the hosts response to the ICMP ECHO_REQUEST packets.
How to ping?
Go cmd type ping {then address}
E.g. ping 192.168.70.14 or ping www.csice.org
Fig: 4.1.1.9 Ping Sweep]
4.2 Scanning & Enumeration:-
Port scanning is the process of connecting to TCP and UDP ports for the purpose of finding what services and applications are open on the target device. Once open, applications or services can be discovered. At this point, further information is typically gathered to determine how best to target any vulnerabilities and weaknesses in the system.
[Fig 4.2.1 Scanning and Enumeration]
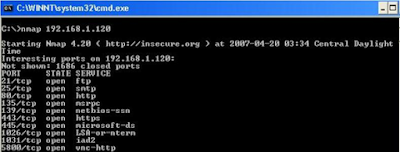
4.2.2 Port Scanning:-
Port scanning is one of the key steps of ethical hacking. Before a system can be attacked, the hacker must determine what systems are up, what applications are running, and what versions the applications are.
Nmap:-
As you might guess, the name “Nmap” implies that the program was ostensibly developed as a network mapping tool. Well, as you can imagine, such a capability is attractive to the folks that attack networks, not just network and system administrators and the network support staff. Of all the tools available it is Nmap that people just seem to keep coming back to. The familiar command line interface, the availability of documentation, and the generally competent way in which the tool has been developed and maintained, are all attractive to us. Nmap performs a variety of network tricks.
[Fig 4.2.3 Nmap]
4.3 Trojans & Backdoors
4.3.1 Trojans:-
A destructive program that masquerades as a benign application. Unlike viruses, Trojan horses do not replicate themselves but they can be just as destructive. One of the most insidious types of Trojan horse is a program that claims to rid your computer of viruses but instead introduces viruses onto your computer.
Main functions of a Trojan:-
- Stealing information's such a password, credit card info, screenshot's etc.... with the help of a key logger
- Disabling firewall and antivirus
- Infect your pc as a proxy server for future attacks
- Generate fake traffic to create DOS attack
- Download spy ware, ad ware etc.......
- Delete your system files
- To create and send spam messages
- Use victim pc as a botnet for Dos attack
Symptoms that may indicate a Trojan infection:-
- Your computer screen flips upside down or inverts
- Your wall paper or background settings change by themselves
- Documents or messages print on your printer by themselves
- Your windows color settings change by themselves
- Your screen saver settings change by themselves
- Your right and left mouse buttons reverse their functions
- Your mouse pointer disappears
- Your mouse moves by itself
- Your mouse starts leaving trails
- Your Windows Start button disappears
- Your computer starts reading the contents of your computer clipboard
- Your Task bar disappears
- Your computer shuts down and powers off by itself
4.3.2 Backdoors:-
Backdoors is also called a trapdoor. It is an undocumented way of gaining access to a program, online service or an entire computer system. The backdoor is written by the programmer who creates the code for the program. It is often only known by the programmer.
4.4 Proxy
A proxy server is essentially a middle computer that site between the attacker and the Victim. To mask your IP under a proxy server to show that you live in a different country and to make yourself untraceable.
[Fig 4.4.1 Proxy]
4.5 Session Hijacking:-
The first thing to do is define session hijacking. Session hijacking takes two significant forms. First of all, it’s finding and taking over an existing network session. This could be something like two or more clients talking to each other. As an attacker, you find that and then get involved and take it over in some way. Or, another possibility is finding a session that maybe isn’t active. Maybe it’s a saved session. Maybe it’s a timed out session. Maybe it’s a session that has some remnants that we could possibly use, and then using that information, those compromises, to re enable or reestablishes that session in a different context. This would be reestablished in the context of the session that was previously going on.
What you are doing is kind of stumbling across something and potentially reinvigorating that in that context, but with us controlling it instead of whoever might have been controlling it in the past. This is really interesting.
Imagine, for example, if you closed a web browser and walked away and someone was able to walk up to your web browser, connect back up to your session that you had with the bank, and not have to type in a username or a password. They just just become you.
4.6 System Hacking
4.6.1 Types of password Hacking:-
There are of four types of password attack:-
1. Passive online attack
2. Active online attack
3. Offline attack
4. Non-technical attack
1. Passive online Attack:-
In passive online attacks an attacker don’t contact with authorizing party for stealing password, in other words he attempts password hacking but without communicating with victim or victim account. Types of passive online attacks include wire sniffing, Man in the middle attack and reply attack.
2. Active online Attack:-
This type of attack can be directly termed as password guessing. An attacker tries number of passwords one by one against victim to crack his/her password.
3. Offline Attack:-
Offline password attacks are performed from a location other than the actual computer where the password reside or were used. Offline attacks requires physical access to the computer which stores password file, the attacker copies the password file and then tries to break passwords in his own system. Offline attacks include, dictionary attacks, hybrid attacks, brute force attack, pre-computed hash attacks, syllable attacks, rule based attacks and rainbow attacks.
4. Non-Technical Attack:-
This type of attacks does not require any technical knowledge hence termed as non-technical attacks. This kind of attacks may include, social engineering, shoulder surfing, keyboard sniffing and dumpster diving.
4.6.2 What is Rootkits??
A rootkit is a type of malicious software that is activated each time your system boots up. Rootkits are difficult to detect because they are activated before your system's Operating System has completely booted up. A rootkit often allows the installation of hidden files, processes, hidden user accounts, and more in the systems OS. Rootkits are able to intercept data from terminals, network connections, and the keyboard.
Root kit helps hackers to maintain hidden access to the system using virus, Trojan horse, spyware etc....
4.6.3 Steganography:-
The art and science of hiding information by embedding messages within other, seemingly harmless messages. Steganography works by replacing bits of useless or unused data in regular computer files (such as graphics, sound, text, HTML, or even floppy disks) with bits of different, invisible information. This hidden information can be plain text, cipher text, or even images.
Steganography sometimes is used when encryption is not permitted. Or, more commonly, steganography is used to supplement encryption. An encrypted file may still hide information using steganography, so even if the encrypted file is deciphered, the hidden message is not seen.
Hacking Tools:-
1. LOPHTCRACK:-
It’s password auditing and recovery software.
Download from: http://1337x.org/torrent/42867/0/ (use torrent client to download)
2. LCP:-
Main purpose of LCP program is user account passwords auditing and recovery in Windows NT/2000/XP/2003.
General features of this product << visit there website>>
Download from: http://www.lcpsoft.com/english/download.htm
KEY-LOGGER:-
It Capture all the keystrokes.
3. USB KEYLOGGER:-
It captures all the keystrokes by using a Usb drive which contain the Usb key logger software.
Download from: http://www.keyghost.com/USB-Keylogger.htm (paided s/w)
4. KEYLOGGER FOR MOBILE:-
Visit: - http://mobihacking.blogspot.com/2011/08/keylogger-for-symbian-s60v3-devices.html
5. SPYWARE:-
It will capture all the events, activities, website visited, keystroke, and screenshots, from a remote machine to our machine through mail
Download from: 1337x.org/torrent/47798/0/ (use torrent client to download)
6. OPENPUFF (STENOGRAPHY TOOL):-
Download from: embeddedsw.net/zip/OpenPuffv340.zip
PDF tutorial: embeddedsw.net/doc/OpenPuff_Help_EN.pdf
5. CONCLUSION
One of the main aims of the seminars is to make others understand that there are so many tools through which a hacker can get in to a system. There are many reasons for everybody should understand about this basic. Let’s check its various needs from various perspectives. A student should understand that no software is made with zero vulnerability. So while they are studying they should study the various possibilities and should study how to prevent that because they are the professionals of tomorrow. Professionals should understand that business is directly related to security. So they should make new software with vulnerabilities as less as possible. Even if the software menders make the software with high security options without the help of users it can never be successful. It’s like a highly secured building with all doors open carelessly by the insiders. So users must also be aware of such possibilities of hacking so that they could be more cautious in their activities. In the preceding sections we saw the methodology of hacking, why should we aware of hacking and some tools which a hacker may use. Now we can see what we can do against hacking or to protect ourselves from hacking. The first thing we should do is to keep ourselves updated about those software’s we can using for official and reliable sources. Educate the employees and the users against black hat hacking. Use every possible security measures like Honey pots, Intrusion Detection Systems, Firewalls etc. Every time make our password strong by making it harder and longer to be cracked.
The final and foremost thing should be to try ETHICAL HACKING at regular intervals.
💜 Agar post Achhi lage to share karna na bhule 💜
💜 Ethical Hacking 💜
पोस्ट अच्छी लगे तो जरूर शेयर करे










No comments
Post a Comment